Cisco and the Serpent’s Tooth
Published on 1 Aug 2005 at 12:00 pm |
4 Comments |
Trackback
Filed under The Cargo Cults of Business, Brain Trust, Technopolitical, Business and Corporation Related, Networking Technology, Information Technology.
I normally prefer to address issues in the networking industry at a more strategic level, but the recent flap over the response to Michael Lynn’s dogged determination to air confidential information at a trade conference begs commentary. What interests me about this situation are the off-the-cuff reactions that seemed to ripple through the various hi-tech industries in the wake of Cisco’s decision to not disclose details of the vulnerability in their products. The Washington Post’s initial take on the situation is evocative, and clearly shows an "anti-censorship" bias in the treatment of the incident. Cnet has a somewhat more even-handed treatment, but even their very page title implies a "retaliatory" position on Cisco’s part. As might be expected for the world’s largest networking vendor throwing its weight around, the tempest in a teapot gained legs in the media, culminating in a gathering storm of pitchforks and torches according to this subsequent Cnet article (warning: Cnet’s proofreading failures waxed scatological, at least at the time of this article’s writing. I guess the columnists are above needing spam-checking software… ![]() ).
).
And so, watching the hacker community cycle up into a dull roar of opprobrium at Cisco, I find myself wondering, "Which part about ‘confidential and proprietary’ don’t these people understand?" We can presume and infer from various comments from the principals involved in the (now supposedly settled) dispute that at no time was the question of whether the "sensitive data" was Lynn’s property in dispute: It most decidedly was never his! Were the context of this situation different, namely, an employee of an American defense contractor disclosing secret– and damaging– military information on say, weapons systems architecture, such treacherous behavior would be resoundingly denounced. The bigger the supposed "vulnerability" ("Look, ma, you can set off an atomic warhead remotely!"), the more treacherous the "whistleblower’s" activity would be viewed as. But because of the context– and, I contend, only because of the context– of the Cisco imbroglio, the violator’s actions come to be viewed as some noble blow in the cause of freedom, and the victims (Cisco and ISS) end up portrayed as overbearing thugs for trying to recover control of their intellectual property.
In what will surely become a mantra on Cargo Cult, you just can’t make this stuff up. Such complete disengagement from the factual proceedings and the ongoing conflation of purely emotional biases into actual policy positions is the meat and potatoes of the very idea of cargo cult business practices. At least on Slashdot, we notice that some of the more level-headed folks figured this out. It’s just insane to think that as an employee you can walk around disclosing whatever confidential information you please in direct defiance of your prevailing legal agreements with your employer and even your employer’s explicit instructions. If the information you disclose could be– or, worse, is– used to cause widespread harm to millions of people, then it’s equally insane to think that you’re not going find yourself doing a legal dance in the criminal courts. As noted by the Slashdot readers, it’s been long established that the first ammendment just doesn’t apply in cases of causing widespread harm, panic, and disruption. And it certainly doesn’t apply when you’ve signed a legal agreement to maintain the confidentiality of information that is under your control and that never in any way ever belonged to you.
This isn’t a case of "whistleblowing", it’s a case of near-criminal misconduct on the part of a (clearly misguided) employee. You can argue till the day is long that Cisco and ISS should have handled this situation differently, that security through obscurity is bunk, that full disclosure of vulnerabilities is the only way to ensure they are addressed, etc. But these arguments are completely irrelevant to the real issue of Lynn’s misconduct in unlawfully disclosing confidential information that did not belong to him. The induction of such orthogonal rhetoric into the issue at hand is cargo-cultism at its finest.
It greatly distresses me that even a portion of the hacker community seems to have been so easily seduced by the mere articulation of rhetoric so near and dear to its heart in the context of a conference venue comprised of security infrastructure stalwarts. Of course, it’s inherently difficult to tell how representative of overall hacker perspective the various media outlets are being. A conspiracy wag could easily imagine all the media coverage of this situation as just an attempt to gin up corporate opposition to the hacker engines of open source, with underground funding to the media outlets coming from Redmond. But, except for myself in this article and the clear-eyed few on Slashdot that I’m aware of, people aware of the real, underlying issues in this situation seem few in the face of the almost-palpable outrage of many Slashdot readers and the media (thinly veiled) at Cisco’s actions. Which brings us full circle to "Which part about ‘confidential and proprietary’ don’t these people understand?"
Part of what boggles my mind at the idea of any of the hacker community championing Lynn’s actions is that he broke a legal agreement for the management of intellectual property. And, hello!, such an agreement is of the same nature and function as all of the open source licensing practices currently in use. How would most hackers react if I grabbed a big blob of GPL’d source code, stripped out all the attributions, used it to shore up my own weak proprietary code, and started selling it as closed source? I don’t know who would get me first, the blogosphere or the army of lawyers that would surely descend upon me. But I can almost guarantee that you wouldn’t see the hacker community rallying around me in support of my free speech rights under the first ammendment. The fact that there are hackers coming out in support of Lynn when he has effectively trod upon all the legally essential principles of the GPL is downright shocking to me. Either I don’t understand the hacker community as well as I like to think I do, or these individuals are in serious need of upgrades to their memetic firewall code.
It would have been nice if Cisco had issued a press release detailing what confidentiality provisions Lynn had violated, but alas, they did not (at least, not as of this writing, according to their corporate web site). At least then, there would have been a public touchstone of their legitimate grievances in this situation, unfiltered by third parties, that might have prevented the cloud of misapprehension. As it was, the reliance on media dispersion of pieces of what was probably more substantive verbal commentary did not serve Cisco well, since the media so far seem to be fomenting an anti-Cisco bias (and why not; in these days of yellow journalism, what better way to move more copy and snag more eyeballs than to dish out dirty laundry on an industry titan).
Personally, I think Cisco’s behavior was downright saintly in light of Lynn’s flagrant disregard for his legal obligations. Notification of the FBI is, for a company of Cisco’s size and means, clearly a CYA move. If they wanted to hammer Lynn with criminal charges, they could easily do it, and given Lynn’s brazen behavior, I doubt it would be difficult to make them stick.
Of course, it’s always our hope here at Cargo to offer helpful prescriptive approaches to prevent a recurrence when something like this happens. But beyond the aforementioned press release (which I sincerely hope Cisco is still working on feverishly in some San Jose cubicle farm), I don’t think there’s a lot that Cisco or ISS could do differently when confronted with such behavior. At a strategic level, though, I think it makes a lot of sense for Cisco to own their righteousness in these events. I think a very effective way to do that would be to use their industry influence to sponsor or, even better, themselves present a series of industry seminars on confidential information management at conferences and other appropriate trade venues. That would allow them to turn this situation to their advantage in the best way possible. By boldly featuring this incident as an example of the flagrant and irresponsible violation of confidentiality agreements, they would be positively communicating their support for the responsible management of intellectual property. Even more important, though, they would be helping raise the industry consciousness as a whole with regards to the foundational criteria for determining best practices in the disclosure of security vulnerabilities. This would leave them in the position of cooperatively establishing, with the hacker community, The Right Thing to Do in a case such as this. That would effectively rebut any afterimage of corporate insularity left by the current tide of disaffection.
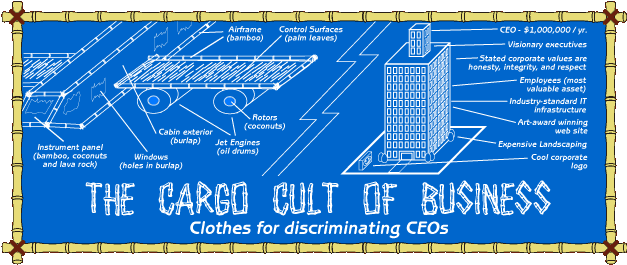
As always, here’s hoping that the perspectives of sanity will yet prevail in this instance, and the bamboo airframes and conflated free speech rhetoric will be spotted for what they are.
——-
Footnote: Journalistic purists may think that for completeness I should confess here my former employment with Cisco and the attendant possibility of bias in Cisco’s favor. However, that’s not the half of it: I have a stated pro-Cisco bias in my entire career that I’ve no plans to change. Nonetheless, if Lynn’s and Cisco’s situations were somehow reversed (and I find that difficult to picture), I wouldn’t hesitate to point out Cisco’s malfeasance. But all this will become clear in subsequent writings about Apple Computer… 
| Computer Recyclers |
|---|
| Pre-Owned Macintosh Computers, Parts, & Service |
|
Clearance iMac G4s & G5s 10% off on all PPC imacs in stock during February. |



July 31st, 2005 at 5:18 pm
Apart from the main thrust of your argument, with which I agree, I think there’s evidence here of a greater misapprehension of what a “right” is.
To over simplify slightly, especially in regard to the bill of rights a right refers to something the federal government can’t do to you. To paraphrase, they can’t prevent you from speaking out, they can’t dictate your religion, they can’t forbid you from associating with those you choose, they can’t disarm you, etc.
The first amendment doesn’t apply to Cisco in any event since they’re not the federal government. Of course, even if it did once you’ve contractually signed away a right you can no longer expect to exercise it without consequences.
August 2nd, 2005 at 1:50 pm
This is a carbon-copy of a post from my blog at MemeStreams:
Title: Cisco and the Serpent’s Broken Tooth (Response)
This is the first comment in the blogosphere about this situation I’ve seen that’s been truly misguided.. I would like to respond to the two sections of this quote I’ve put in bold face.
First, it would be Mike Lynn who would catch you, or someone like him. As proof of this, I offer the recent situation where Mike Lynn did the analysis that proved CherryOS stole the code for its emulator product from the PearPC open source project. I pointed this our earlier. Here are a few quotes from his article:
As far as our memetic firewalls go, we are working on that, and have been for quite awhile. Mike analysis on the CherryOS situation was posted here on MemeStreams.
August 3rd, 2005 at 8:36 pm
All your points on Intellectual Property are valid. Hence, I opted not to attack your argument from that perspective. I am also not in the anit-IP crowd. I think to get the carrier firmly up, we need to establish more facts. It appears that incorrect assumptions lie at the heart of the differences in our views.
Mike never had the IOS source code. Cisco never gave it to him; he was not under NDA to have it. He did not violate any of their rights to protect their source code. Mike did his research by disassembling the publicly available IOS images. This was a case of reverse engineering. If anything, Mike’s legal liability lied in exposing trade secrets, but not due to any access to (Cisco) proprietary information. Both you and I could easily have access in a “virgin” manor to what Mike based his research on. I assume that both Cisco and ISS (and their respective legal teams) did not feel they were standing on firm enough ground to go after Mike based on this tactic. The dogs smelled blood and were barking, but they were kept on the leash. The reason certainly wasn’t a feeling of mercy on the part of Cisco.
Once we get here, we come full circle again. And its a big circle. The ends meet at places like the old DeCSS situation. If you own the chattel (odd context to use that term, I know), do you have the right to take it apart and figure out how it works? Can you share that information? If the law is vague, where do ethics supplement the pre-legal argument? If this situation winds up being framed in that light, its the DMCA we have to look to. If you want a laugh, think about if coming up with an exploit qualifies as “necessary to achieve interoperability of an independently created computer program.”
I also do firmly believe that Mike’s statements are grounded in fact when it comes to matters like “China has this.” The big picture could best be described as “huge” if you acknowledge that. Thinking about the problem honestly feels like wargaming to me.
The general option of the hacker (read: security, not criminal) community is that Cisco has a broken security culture. They need a wake-up call like this to bring positive change to it. I think they will be successful with it in the long term too. I’m also not a member of the “all corps are dumb” crowd. At worst, I prefer to think of them (us?) as “slow”. ISS on the other hand, I don’t have such kind words for. Please take a look at this post on my blog which contains a link to and some excerpts from Mike’s interview with Wired.
That made me outright angry. It also raised some serious questions, which I am not going to put forth in a public forum. Bonus points if you can figure them out…
August 4th, 2005 at 12:00 am
Rattle,
Well. I suppose this is the point where I have to demonstrate adherence to the precepts of logical discouse. I’ll do my best…
Your statements about Mr. Lynn’s access to IOS source code are evocative. This whole situation is a study in media distortion, and the attempt of individuals to get the facts in the teeth of shotgun fact reporting by the purported “professionals.” Nonetheless, there are puzzling conflicting reports, specifically this one from Network World. The salient point from the NW article is this: “Lynn acknowledged in a settlement reached Thursday that he had broken confidentiality agreements and by week’s end he and his lawyer were delivering sensitive materials and software related to the router exploit into the hands of Cisco lawyers.”
It is sine qua non these days for large corporations to construct legal agreements that overreach, so as to assert (not necessarily achieve) as much control as possible. Lynn clearly had access to some sensitive material, and so he was clearly operating under some sort of NDA. My guess is that in the course of Cisco getting engaged, he signed something. I don’t know how thoroughly he reviewed what he was asked to sign. I don’t know if he consulted with counsel before signing it. Chances are, since he was “acting under color of his employer”, he did what I would have done and just signed on the dotted line, trusting ISS’ counsel to be on their game. But however it happened, it still looks to me like he ended up legally handcuffed. Judging from Cisco’s actions, the legal handcuffs were sufficiently large to allow Cisco to assert control over all of his IOS research.
I’ll hazard an apparent tangent for a moment and address your point about “publicly accessible IOS.” I’m really pretty sure that Cisco doesn’t consider their code– source or binary– to be “publicly accessible.” When you get it from them, it has a typical deforestation project of a EULA along with it. I’m certain that Cisco would assert that such control extends to hardware devices of theirs, whether purchased from them or sniped in an eBay auction. I’ll come back to this point shortly.
Now, given that Lynn later acknowledged breaching confidentiality agreements (of some sort, but per your points not necessarily for IOS sources), when he decided to cross the line he effectively threw himself to the lions. There is indication in his own words that he recognized that this was the case.
And this is where I start to have some issues. The venerable Henry Thoreau is a trendsetter in matters such as these: he determined that defiance of the men with guns was a moral imperative, and he did his time. I’ll accept that Mr. Lynn believed (irrespective of the robustness of such belief) that he was in one of those situations. I have been faced with similar dilemmas, tho nothing on that scale. But part of the decision to defy is an inherent recognition of the consequences that will ensue from one’s defiance. I don’t think its reasonable to wreck a train as large as the one at issue here, and expect to dodge all the bullets. Furthermore, dodging is one thing, but concession is another. Maybe Mr. Lynn simply confessed to the sins of violating agreements because he felt that the men with guns left him no choice.
But if that’s so, then I think still less of him. If his conduct was truly on the up-and-up, then no quarter should have been given, and certainly not in the form of admitting that you broke the trust to accomplish your goals. I’m not very big on the means justifying the ends, and if my guesswork here is close to the mark, then it looks like that may well be what happened.
But it’s just guesswork. I don’t know Mr. Lynn. My information sources are irreparably filtered, one way or another. And Cisco, who I still think was in a position to effectively re-rail the train, have been a sphynx compared to what (IMNHSO) they ought to be saying and doing. Nonetheless, from where I’m sitting it still looks as if Mr. Lynn made legal commitments, and then decided to breach them, supposedly for the greater good.
And tying back to my original points, if Cisco really did have legal control over the information Lynn disseminated, then his actions are reprehensible. It was Cisco’s call, not his, as to how that information should be propagated.
Sure, you’re absolutely correct: Cisco needs to improve their vulnerability management. I think they’re one of the best out there, but even if that isn’t a low bar to pass, there is always room for improvement. But the fact that Cisco was ham-handling the situation doesn’t change the fact that it was their legal right to do so. Mr. Lynn could easily have raised awareness of the situation; “Hey! Everybody! I can’t tell you why, but this bug, it’s way worse than you can imagine!”. Based on extant accounts, he could even have said “This problem will allow an attacker to gain full access to the device. I’m sorry that due to my prevailing confidentiality agreements I’m not at liberty to tell you how.” But that isn’t what he did. Instead, he broke those agreements. And in so doing, he set off a domino chain of inevitability. Cisco was already twitchy, whether from the conference talk suddenly coming onto some executive’s radar or the legal eagles squawking. But once the glass broke, the eagles swooped, and from there on out, it was the lawyers’ playbook determining the titan’s next steps. They are a big corporation, and even though they are one of the best on the planet, it should not come as any suprise that they use big corporation damage control when something like this breaks loose.
As to ISS, well, what is there to say? Taking Lynn’s account in the Wired article you mention as robust, these guys are up for a Cargo Cult Manifest Masquerade award. If Dice isn’t chock full of ISS resumes right now, then their drones need to wake up and smell the backstabbing. Sure, ISS was within its rights to command Lynn to stand down. But just because its legal, doesn’t make it right. Kow-towing in an effort to curry favor, even with Cisco, is pathetic. But let’s fisk a little further. ISS orders Lynn to reverse-engineer the code. When Lynn goes public as an individual, wrath descends on him for violating the sanctity of IOS. But wait a minute, what about ISS. I mean, hello!, they’re the ones who ordered him to do the reverse engineering in the first place. Why aren’t they in the crosshairs? Just because they didn’t go public? Then what’s the message? “It’s OK to reverse engineer stuff, just as long as you don’t tell anybody”? That hardly seems consistent. And in terms of hanging Lynn out to dry to save their own scrawny necks, its wildly unjust. But it also brings us round that circle…
I mentioned the IOS EULA, and the situation of purchasing a hardware device that has the IOS code in flash. You mentioned the DeCSS debacle, and the DMCA. And rightly so, because this is where it gets interesting.
At the “strategic level”, I prefer to just avoid any discussions about the DMCA entirely. That goes doubly true for the various campaigns of racketeering, thuggery and extortion perpetrated by Big Media. In the case of the copyright issues, by my algorithm (”The Constitution says copyright can be used for commercial purposes and citizens can say whatever they want if its noncommercial, which part about this don’t you understand?” it’s all so wildly unconstitutional that its a wonder the Earth’s magnetic field hasn’t reversed from all the Framers spinning in their graves. In the case of Big Media, they are oh-so-guilty of violating every racketeering and extortion statute on the books that they should be doing time. And in the case of the judges who’ve chosen political expediency over the precepts of the Constitution, well, they’ve violated their oaths and should be deported for treason. But, alas, my quiver of lightning bolts remains empty, and so lacking legions of terror to bring these scoundrels to justice, I expect the situation will only get worse.
But on the tactical level, yeah, the DMCA looks like the other shoe in this whole thing to me. I think Cisco is steering clear of it because they rightly realize going there would be a disaster for them, not just PR-wise, but in terms of changing the soul of the company and alienating legions of employees and customers. The lawyers wouldn’t have let that one go, so I’m just taking it as read that they won’t try to apply it. But the storm’s not over, and I could be wrong… As far as Mr. Lynn goes, however, with all this in mind it just shouldn’t matter who he was acting for when he did the reverse engineering, because absent secret treaties from Cisco, it should have been perfectly legal. As best I can tell, that’s your point, and as you can see (modulo the question of what legal agreements were in place), I’m happy to concur.
In closing, I’ll make this stipulation: If it is true that Mr. Lynn’s reverse engineering proceeded entirely in a “clean room” fashion, then I will agree that to that extent he deserves the full protection of the law, and not its censure. I deeply question the issue of what agreements he did violate, and at this point I’m still not convinced he didn’t fall from grace in the course of his pursuit of raising consciousness about the exploit. But taking Mr. Lynn out of the picture, I most certainly believe that reverse-engineering is an inherent right directly derived from the right to own chattel, even as you say. And the right to publish those results– to the extent they do not consitute commerce– is protected speech under the First Ammendment.
With thanks for the great discussion,
Paul
P.S. I can guess at least some of the bonus points…